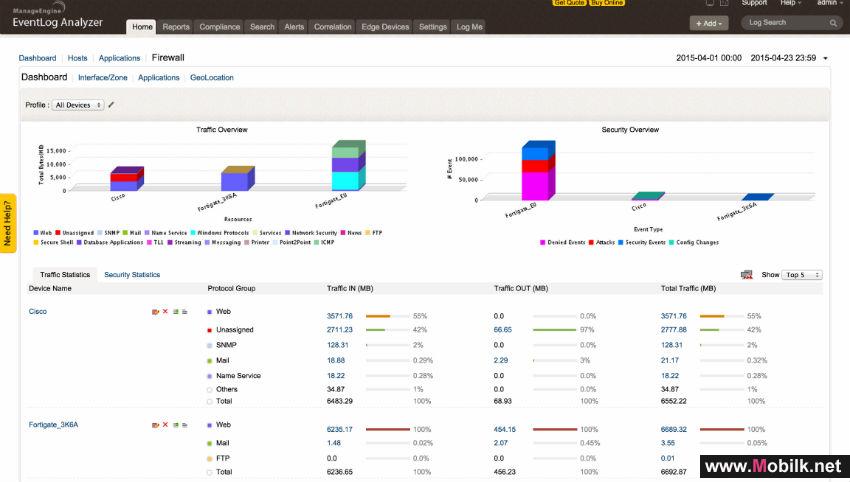
ManageEngine Releases Latest Version Of EventLog Analyzer With New Security Device Configuration Management Capabilities At GISEC 2015
Mobilk - ManageEngine, the real-time IT management company, today announced the Firewall Analyzer add-on for EventLog Analyzer, the company’s log analysis solution at GISEC 2015. The new add-on enhances EventLog Analyzer with multi-vendor security device and configuration management features to help IT security administrators monitor and analyze security incidents better. Admins can now seal security loopholes due to firewall misconfigurations, monitor network traffic and bandwidth usage, and propagate and analyze security incidents from log sources across the network — all from a single, central console.
As hacking techniques get more sophisticated, detecting cyber threats at the initial stages is becoming difficult. Despite protecting the network with multi-level security, businesses continue to face cyber threats. The deployment of discrete, disconnected perimeter security systems, such as firewalls, intrusion prevention systems (IPS) and intrusion detection systems (IDS), follows a granular approach to threat mitigation and also generates voluminous amounts of log data, which is often mistaken as an indicator of compromise. To track down security threats in the initial stages, companies need a unified security console that can accelerate responses to data breaches.
“Perimeter security devices have always been the crucial source in identifying early signs of network security anomalies,” said Pravin Kumar, product manager at ManageEngine. “In most cases, as a complement to log analysis, constant monitoring of security devices’ configuration changes helps contain attacks at the earliest stages. Our new add-on provides instant access to firewall device configuration details, network traffic and bandwidth usage details, and log data from sources across the network by collating them in one central location.”
EventLog Analyzer Firewall Analyzer Add-On Highlights
•Combats external security threats better: The add-on provides intuitive geo-location reports that help identify the origin of virus attackers and spammers, top hosts that are affected by the attacks and more.
•Unmasks shadow IT operations: The Firewall Analyzer add-on enables security administrators to monitor shadow IT operations that throttle the company’s bandwidth. Admins can also monitor the bandwidth consumed by unauthorized cloud-controlled applications and services with the intuitive graphical dashboard. The solution also provides detailed reports for user-wise bandwidth usage.
•Meets compliance requirements for security device configuration management: The solution helps meet the requirements of industry’s best firewall practices such as SANS, NIST, and NERC – CIP, besides the compliance requirements around security device configuration management.
•Provides contextual information to track down real security attack attempts: The integration provides security device configuration change details such as what rule was changed, when the change was made, who made the change and from where.
•Provides clear visibility into network bandwidth and traffic usage: The Firewall Analyzer add-on provides detailed information on inbound and outbound traffic and application bandwidth usage so that security admins gain better visibility on what is choking the bandwidth.
Pricing and Availability
The Firewall Analyzer add-on to EventLog Analyzer is available as a beta download. EventLog Analyzer customers can try it via the beta program at http://www.eventloganalyzer.com/firewallintegration.html. EventLog Analyzer starts at $3,495 for 50 log sources.
Events
TikTok MENA hosted an insightful panel discussion on May 29, delving into the important topics of online safety and digital well-being for teens. The..
Events
Developway company has announced the launch of the "978ai.com" guide for artificial intelligence tools in both Arabic and English, to meet the..
Events
As enterprises in the Middle East progress in their digital transformation mindset, Charles Yang, SVP of Huawei and President of Global Marketing..

 Vodafone Oman
Vodafone Oman Emirates Telecom
Emirates Telecom  Ooredoo Om
Ooredoo Om Ooredoo Qa
Ooredoo Qa stc Bahrain
stc Bahrain Orange Egypt
Orange Egypt Mobily
Mobily Zain Jo
Zain Jo omantel
omantel STC
STC Emirates Du
Emirates Du Asiacell
Asiacell Etisalat Egypt
Etisalat Egypt  Telecom Egypt
Telecom Egypt jawwal
jawwal Orange Jo
Orange Jo Umniah
Umniah Zain Sa
Zain Sa Bahrain Batelco
Bahrain Batelco Zain Bh
Zain Bh Wataniya palestine
Wataniya palestine Kuwait Viva
Kuwait Viva  Zain Kw
Zain Kw Vodafone Qa
Vodafone Qa MTN Syria
MTN Syria Syriatel
Syriatel Sabafon
Sabafon Zain Iq
Zain Iq MTN Yemen
MTN Yemen Ooredoo Kw
Ooredoo Kw Vodafone Egypt
Vodafone Egypt  Samatel
Samatel Huawei
Huawei Samsung
Samsung MOTOROLA
MOTOROLA Alcatel
Alcatel Lenovo
Lenovo LG
LG Nokia
Nokia Sony Ericsson
Sony Ericsson HTC
HTC BlackBerry
BlackBerry Siemens
Siemens Acer
Acer Sony
Sony Asus
Asus VK
VK APPLE
APPLE BenQ-Siemens
BenQ-Siemens Sagem
Sagem Eten
Eten HP
HP Panasonic
Panasonic Amoi
Amoi Toshiba
Toshiba Sharp
Sharp Sonim
Sonim Bird
Bird Mitac
Mitac Philips
Philips Pantech
Pantech Vertu
Vertu Micromax
Micromax Maxon
Maxon Haier
Haier I-mate
I-mate Gigabyte
Gigabyte I-mobile
I-mobile Kyocera
Kyocera BenQ
BenQ Microsoft
Microsoft Telit
Telit Connect
Connect Sendo
Sendo SEWON
SEWON Mitsubishi
Mitsubishi DELL
DELL Thuraya
Thuraya NEC
NEC Qtek
Qtek Be
Be Neonode
Neonode Bosch
Bosch MWG
MWG Palm
Palm XCute
XCute Fujitsu Siemens
Fujitsu Siemens WND
WND INQ
INQ Innostream
Innostream O2
O2 Benefon
Benefon Google
Google